Safeguard Your Online Store
Empowering Online Merchants with Comprehensive Cybersecurity, Firewall, and DDoS Defense.
Empowering Online Merchants with Comprehensive Cybersecurity, Firewall, and DDoS Defense.





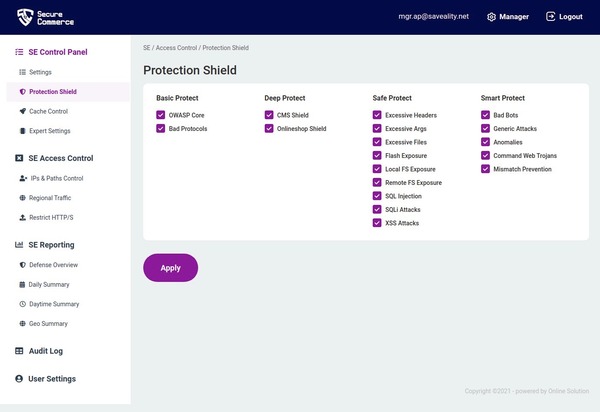
Online store falls victim to a targeted denial-of-service attack by unfair competitors, blackmailers or contract hackers. DDoS attacks usually occur in waves at the beginning, temporarily leading to noticeable performance optimization losses or interruptions and even downtimes of the online offering. The attack is then usually increased in frequency up to permanent interruption for several hours or days.
Payment data or addresses of the online store customer base end up in the hands of third parties, are published, resold on the darknet, misused for phishing attacks or offered for repurchase by blackmailers. The most common reasons for data leaks from online stores are configuration errors, cloud and server vulnerabilities, and targeted hacker attacks.
Increasingly, online stores are being attacked at payment processing interfaces. Intruders can redirect customers to phishing sites when paying with Paypal/Klarna/immediate gateways or request payment to different accounts in your name.
Customer places his order and pays for the item while the attacker overwrites the shipping address unnoticed by manipulating the shipping processing interface in the online store. Despite shipping, the goods do not reach the customer.
Particularly in the case of B2C offers with high-value items, targeted attacks on product price data are worthwhile for hackers, whereby orders at incorrect prices usually go undetected. In addition, fraud through vouchers and coupons is popular with attackers and low-risk. Security Solution for online store software: security for
Since recent incidents on the online shop system Volusion and the continuation at Shopify, e-commerce operators are sensitized. Malware infects and spreads preferably via online stores due to the fast spreading thanks to the high trust of customers. Unfortunately, this very thing leads to the loss of trust for the online store.